The Ultimate Guide to Vulnerability Management: Safeguarding Your Digital Assets
In today’s rapidly evolving digital landscape, cybersecurity threats are more prevalent than ever. As organizations rely increasingly on technology, the need for effective vulnerability management has become crucial. This article will delve into what vulnerability management is, why it matters, and how you can implement a robust program to protect your digital assets.
What is Vulnerability Management?
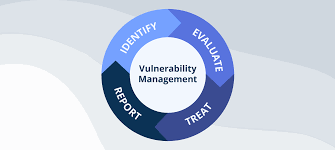
Vulnerability management is the ongoing process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and software. It involves a systematic approach to discovering weaknesses that could be exploited by cybercriminals, enabling organizations to mitigate potential risks before they can be leveraged in an attack.
Why Vulnerability Management is Crucial
1. Proactive Defense: By identifying and addressing vulnerabilities before they are exploited, organizations can proactively defend against potential cyberattacks.
2. Regulatory Compliance: Many industries are subject to regulations that require effective vulnerability management practices to ensure data protection and security. Failure to comply can result in hefty fines and reputational damage.
3. Risk Reduction: Vulnerabilities present significant risks to organizations, from data breaches to service disruptions. A well-managed vulnerability management program helps reduce these risks by ensuring that security gaps are closed promptly.
4. Cost Efficiency: Addressing vulnerabilities early can save organizations from the much higher costs associated with data breaches, including loss of business, legal fees, and remediation expenses.
Key Steps in Vulnerability Management
1. Asset Discovery and Inventory
– The first step in vulnerability management is to identify all assets within the organization’s network. This includes hardware, software, and cloud services. Creating a comprehensive inventory ensures that no asset is overlooked.
2. Vulnerability Scanning
– Regularly scanning your network for vulnerabilities is essential. Automated tools can scan for known vulnerabilities, misconfigurations, and outdated software that may expose your systems to threats.
3. Risk Assessment and Prioritization
– Not all vulnerabilities carry the same level of risk. After scanning, vulnerabilities should be assessed based on factors like the potential impact, exploitability, and the criticality of the affected asset. This helps in prioritizing which vulnerabilities need immediate attention.
4. Remediation
– Once vulnerabilities are identified and prioritized, the next step is remediation. This can involve patching, configuring systems securely, or implementing compensating controls. It’s vital to address high-priority vulnerabilities as quickly as possible.
5. Verification and Monitoring
– After remediation, it’s important to verify that the vulnerabilities have been effectively addressed. Continuous monitoring is also necessary to ensure new vulnerabilities are detected and dealt with promptly.
6. Reporting and Documentation
– Documenting the entire vulnerability management process is crucial for accountability and compliance. Reports should include details of identified vulnerabilities, their risk assessments, remediation actions taken, and any remaining risks.
Best Practices for Effective Vulnerability Management
1. Automate Where Possible
– Use automated tools to regularly scan your systems for vulnerabilities. Automation not only speeds up the process but also reduces the chance of human error.
2. Stay Updated
– Keep your software and systems updated with the latest patches and security updates. Subscribe to threat intelligence feeds to stay informed about emerging vulnerabilities.
3. Integrate with Patch Management
– Vulnerability management should be closely integrated with patch management to ensure that vulnerabilities are quickly and efficiently patched.
4. Regular Audits
– Conduct regular audits of your vulnerability management process to ensure that it remains effective and aligned with industry best practices.
5. Employee Training
– Train your employees on the importance of cybersecurity and their role in vulnerability management. This includes educating them on recognizing and reporting potential security threats.
Conclusion
Vulnerability management is a critical component of a robust cybersecurity strategy. By systematically identifying, assessing, and addressing vulnerabilities, organizations can significantly reduce their risk of cyberattacks. Implementing a well-structured vulnerability management program not only protects your digital assets but also ensures compliance with industry regulations and standards.
For organizations looking to safeguard their networks, investing in vulnerability management is not just a best practice—it’s a necessity. Stay ahead of cyber threats by implementing these strategies and ensuring that your systems are as secure as possible.